Security Threats to Face Authentication and FaceStation 2 Technology
Apple recently released its most ambitious product, the iPhone X, in celebration of the 10th anniversary of the release of the first iPhone. The iPhone X especially stands out with its introduction of Face ID, a face authentication technology to replace the fingerprint recognition technology (Touch ID). According to Apple, Face ID will recognize a user’s face wrongly only once in 1 million times, an immense improvement over the once in 50,000 times probability of Touch ID.
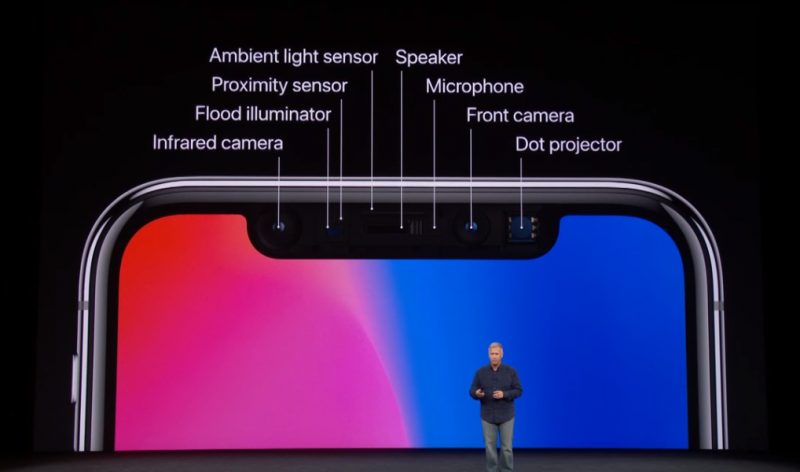
The front side structure of the iPhone X. Face ID uses the infrared camera, flood illuminator, and dot projector. - From Apple -Introducing iPhone X
However, authentication through face authentication is actually as prone to spoofing as fingerprint-based methods. The press was quick to point out after Face ID was announced that it would be easy to recreate through 3D rendering the faces of well-known politicians or actors that are often exposed in photos or videos as there is a great amount of data available on them. 3D printers, which are used to build face structures, are also no longer hard to find. They can be commonly found on the online shopping mall like Amazon.
To prove such spoofing is possible, Bkav, a security company based in Vietnam, succeeded in spoofing Face ID with a face mask it created. The mask’s face structure was created using a plastic mask and silicon, and an additional application of paper and makeup was enough to bypass authentication.
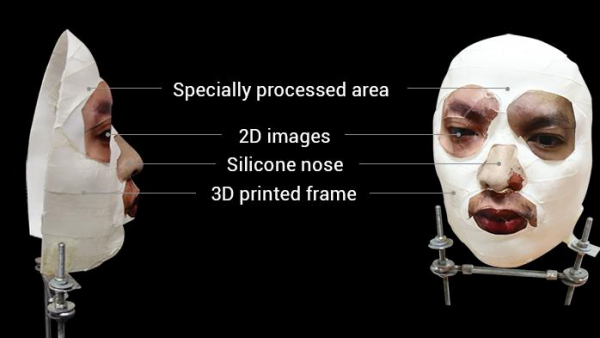
Mask used by Vietnamese security company Bkav to spoof Face ID - From Bkav.com
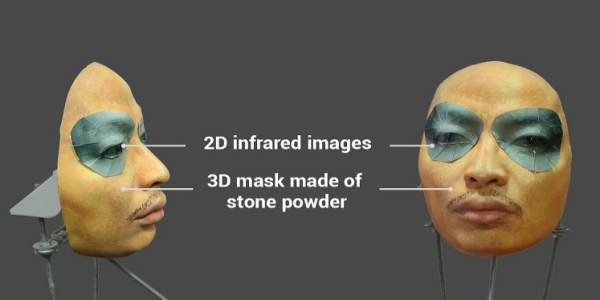
New mask used by Vietnamese security company Bkav to spoof Face ID - From Bkav.com
Then what about Suprema’s FaceStation 2, which also authenticates users with face authentication?
Is its security also vulnerable to similar methods?
FaceStation 2's Advanced Face Authentication Technology
FaceStation 2’s face Authentication method functions differently from the iPhone X's.
The mask the Bkav used to spoof Face ID has eyes, a nose, and a mouth built to resemble an actual person’s, but the remaining parts of the face are made of plastic. Through this information, it can be inferred that Face ID uses 3D modeling data and True Depth technology in its authentication process.
FaceStation 2, on the other hand, not only uses 140 near-infrared (NIR) LEDs to extract 3D feature data, but also uses an algorithm to produce various numerical values from the infrared light reflected off of the face. These values include those related to skin tone and skin texture values, which are helpful in distinguishing between similar faces. This special hardware and algorithm render the mask built by Bkav useless when tested against FaceStation 2’s authentication system.
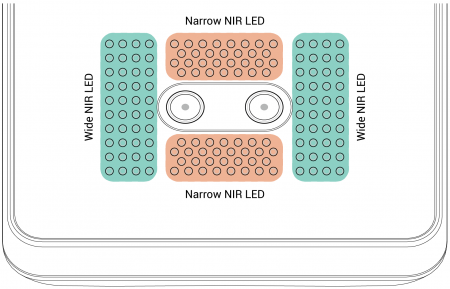
FaceStation 2’s multi-bank NIR LED structure
FaceStation 2 also uses a matching score when executing face authentication. The matching score is a calculation of the match between a pre-registered face template and the actual face to be authenticated. The score helps guard FaceStation 2 against spoofing, as a low value is produced if the mask used in spoofing does not use a 3D model that exactly matches the actual face.
FaceStation 2 was recognized for its technological advancement at the 2017 Detektor International Awards, and was awarded the Best Product Award in the ID & Access category.

FaceStation 2 combines Suprema’s most state-of-the-art algorithm and hardware to provide a new contactless authentication experience, with a greater variety of features and increased performance.